Cyber security threats are a constant concern for businesses of all sizes. Data breaches, malware attacks, and phishing scams can disrupt operations, damage reputations, and result in significant financial losses. Effective defensive cyber security strategies involve the use of technology, processes, and protocols to protect an organisation’s computer networks, devices, and sensitive data from malicious attacks.
Defensive cyber security is an essential part of any modern security strategy. As threats to organisations become increasingly sophisticated, it is crucial to have effective defensive measures in place to protect sensitive data and critical systems. Defensive cyber security is an approach to security that focuses on preventing, detecting, and responding to cyber threats and ensuring your organisation’s assets remain secure. The key lies in being able to answer these five questions:
The first step in any cyber security strategy is a thorough risk assessment. This foundational step involves identifying vulnerabilities within your systems by recognising what data, systems, and hardware need protection. This includes customer data, financial records, intellectual property, and critical infrastructure. Assessing potential threats, such as malware, phishing attacks, ransomware, and insider threats, is crucial. Additionally, evaluating weaknesses in your current security posture, like outdated software, weak passwords, and unpatched systems, helps prioritise security measures and allocate resources effectively. Regular risk assessments also provide a baseline to measure the effectiveness of implemented security controls.

Strong password policies are essential to prevent unauthorised access to your organisation. Weak passwords are a common entry point for attackers, so to address this, you should enforce password complexity with a mix of uppercase and lowercase letters, numbers, and special characters, as well as a password length that is a minimum of 14-16 characters. Discourage common words and phrases, and instead of changing passwords every 60-90 days, it is better to use strong, unique passwords (to prevent password reuse) for each system and enforce Multi-Factor Authentication. Multi-Factor Authentication (MFA) adds an extra layer of security to this by requiring multiple forms of verification, such as a password and a one-time code sent to a mobile device. You can also consider using password managers to assist employees in generating and storing complex passwords securely.



EDR tools are critical for monitoring, detecting, and responding to threats on endpoints like desktops, laptops, and mobile devices. EDR solutions provide real-time visibility into endpoint activities, enabling quick detection and response to suspicious activities. They help identify advanced threats, contain incidents, and facilitate forensic investigations. By integrating EDR tools with other security measures, your organisation can enhance its overall security posture and reduce the time it takes to detect and respond to threats.


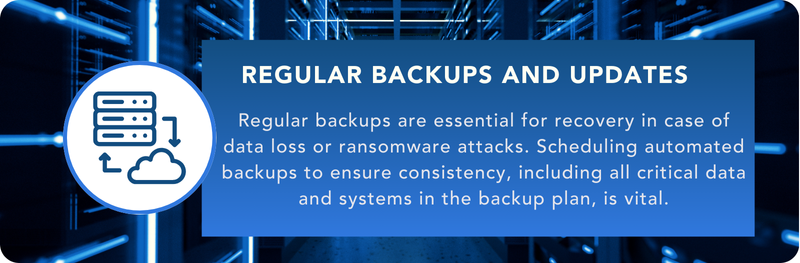
Cyber security threats are a constant battleground for businesses, but by taking action and having these strategies in place, you are taking a proactive stance in protecting your business and its assets. Remember, cyber security is an ongoing process. You can protect your organisation, reputation, and valuable data by staying vigilant and adapting your strategies as threats evolve.
In our next security article, we’ll look at the different offensive cyber security strategies every organisation needs to improve its security.
At Cyberlogic, we offer a comprehensive suite of cyber security solutions, including penetration testing, vulnerability management, remediation solutions, and SOC services. To find out more, visit the Security Solutions page on our website or email us at [email protected].
Secure managed IT services for SMBs and Corporates.
Full-service cyber security for organisations of all sizes.
Data landscape optimisation that enables fact-based decisions fast.
Hybrid, Public, and Private Cloud services for the future, today.
The latest from our technology partners.
Ad hoc licenses from all major software providers.
Flexible payment solutions to enable scale without compromising cashflow.
Sign up to receive our insights directly to your inbox.
The Difference Between Penetration Testing and Red Teaming: What Your Business Needs to Know